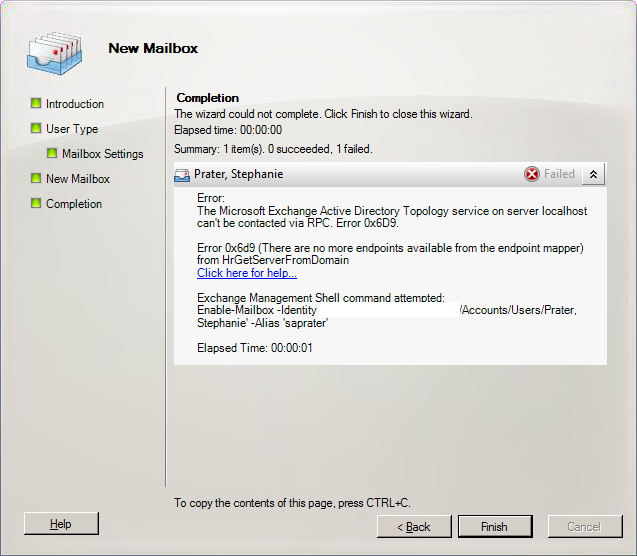
Checkpoint Endpoint Security Failed To Topology
Endpoint Connect Installation / Troubleshooting Guide. Failed to download topology. Endpoint Connect fails to connect to NGX. On the R70 Security. Check Point customers also receive preemptive protections via our product lines (occasionally before a vendor fix is released). It is, therefore, no surprise that we decided to audit WordPress, resulting in our discovery of these critical issues. This appears to be a corrupt client. Microsoft.office.interop.excel 2007. You can fix this easily by doing this: Add/Remove Programs>>>Highlight Checkpoint VPN>>> Click Repair.
Attention, Internet Explorer User Announcement: Jive has discontinued support for Internet Explorer 7 and below. In order to provide the best platform for continued innovation, Jive no longer supports Internet Explorer 7. Jive will not function with this version of Internet Explorer. Please consider upgrading to a more recent version of Internet Explorer, or trying another browser such as Firefox, Safari, or Google Chrome.
Checkpoint Endpoint Connect 'Failed to download Topology'. Endpoint Connect terminates with 'Failed to download Topology. Kangoku senkan english patch. And we dont have R70 Security. Security Gateways running with Cooperative Enforcement behave unpredictably when the Endpoint Security Management Server is down. Therefore, when you shut down or restart an Endpoint Security Management Server that is part of a Cooperative Enforcement environment, first set the Security Gateways to run Cooperative Enforcement in Monitor Only mode.
(Please remember to honor your company's IT policies before installing new software!) • • • •.
Checkpoint Smart Endpoint
Secure data at rest, in use and in transit on endpoint devices Most corporate laptops and PCs store proprietary data on their hard drives, and many users regularly work outside of a secure corporate environment. A data breach from a lost, stolen or compromised laptop can result in costly fines, lawsuits and lost revenue.
Bypass Checkpoint Endpoint Security
Full Disk Encryption secures the entire hard drive. Media Encryption and Port Control secure removable media. Capsule Docs enables organizations to seamlessly protect documents, ensuring access for authorized users only. Remote Access VPN provides secure access to corporate resources when traveling or working remotely. Limba romana manual pentru studentii straini pdf.
Secure endpoint devices from zero-day and advanced threats Threats from malware like viruses, worms and bots change constantly. Users are targets of phishing emails that may contain links to websites infected with this malware. To prevent these new and emerging threats, IT departments need comprehensive security even on endpoint devices no matter where they go. With Check Point SandBlast Agent, security teams can now defend end-user systems against zero-day threats, bot communications with Command and Control servers and other advanced attacks Check Point Anti-Malware further helps to efficiently detect malware with a single scan.